Web Application Firewall Market Introduction
The global web application firewall market size reached approximately USD 5.76 billion in 2023. The market is further projected to grow at a CAGR of 16.7% between 2024 and 2032, reaching a value of USD 23.23 billion by 2032.
These staggering figures underscore the critical role that Web Application Firewalls (WAFs) play in modern cybersecurity. In an era characterized by an ever-evolving threat landscape, the protection of web applications and sensitive data has become paramount. In this comprehensive guide, we will explore the importance of Web Application Firewalls in addressing the challenges posed by modern cybersecurity threats.
Understanding Modern Cybersecurity Threats
To comprehend the significance of Web Application Firewalls, it is essential to first understand the nature of modern cybersecurity threats. Cybercriminals have become increasingly sophisticated, and their tactics continue to evolve. Data breaches, SQL injection attacks, Cross-Site Scripting (XSS) exploits, and other forms of web application attacks have become alarmingly common. According to recent statistics, these attacks have been on the rise, leading to severe consequences for businesses and individuals alike.
Web application attacks can result in data breaches, financial losses, damage to an organization's reputation, and legal repercussions. These attacks target vulnerabilities in web applications, exploiting them to gain unauthorized access, steal sensitive information, or disrupt services. As the volume and complexity of attacks grow, organizations must employ robust cybersecurity measures to safeguard their web applications and data.
Get a Free Sample Report with Table of Contents@ https://www.expertmarketresearch.com/reports/web-application-firewall-market/requestsample
The Role of Web Application Firewalls
Web Application Firewalls serve as a critical line of defense against modern cybersecurity threats. But what exactly are they, and how do they work?
What is a Web Application Firewall?
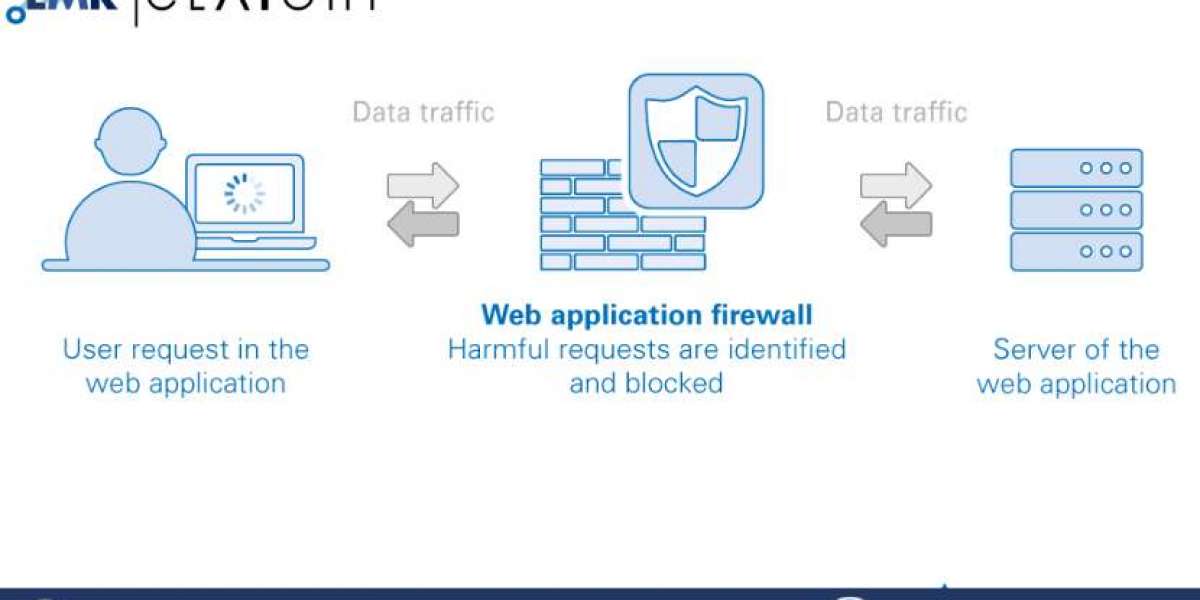
A Web Application Firewall (WAF) is a security solution designed to protect web applications from various online threats. It acts as a shield, standing between web applications and potential attackers. WAFs are equipped with a set of rules and policies that monitor incoming web traffic. They inspect each request and response to identify malicious patterns, abnormal behavior, and potential vulnerabilities.
How Does a WAF Work?
WAFs employ several techniques to protect web applications:
Traffic Inspection:
WAFs inspect all incoming and outgoing web traffic. They analyze the data packets, headers, and payloads to identify potential threats. This deep inspection helps in recognizing known attack patterns.
Filtering:
WAFs use a set of predefined rules to filter out malicious traffic. These rules can include signatures of known attack types, IP addresses associated with attackers, and patterns that are indicative of attacks.
Behavior-Based Analysis:
Modern WAFs often incorporate behavior-based analysis, using machine learning and anomaly detection algorithms. They monitor the normal behavior of web applications and trigger alerts or blocks when deviations are detected.
Key Features and Capabilities of WAFs
Web Application Firewalls come equipped with a range of features and capabilities that make them indispensable in the fight against cyber threats.
Signature-Based Detection:
One of the fundamental features of WAFs is signature-based detection. This mechanism relies on a database of known attack patterns. When a request matches a known signature, the WAF can take appropriate action, such as blocking the request or generating an alert.
Real-Time Monitoring and Threat Detection:
WAFs provide real-time monitoring of web traffic. They constantly analyze incoming requests and outgoing responses, ensuring that any suspicious activity is promptly identified and addressed. This real-time threat detection is crucial for preventing attacks before they can cause damage.
Customization and Policy Management:
WAFs are highly customizable, allowing organizations to tailor their security policies to their specific needs. Administrators can define rules, exceptions, and whitelists to ensure that legitimate traffic is not blocked while malicious traffic is stopped.
Considerations When Choosing a Web Application Firewall
When selecting a Web Application Firewall solution for your organization, several critical factors should be considered.
Scalability:
Ensure that the chosen WAF can scale to meet your organization's growing web traffic and application demands. Scalability is crucial to maintain performance and security as your business expands.
Deployment Options:
Evaluate whether the WAF can be deployed on-premises, in the cloud, or as a hybrid solution. The deployment method should align with your infrastructure and security requirements.
Ease of Management:
Consider the user-friendliness of the WAF's management interface. A well-designed dashboard and intuitive configuration options can streamline the administration of security policies.
Cost Considerations and ROI:
Determine the total cost of ownership, including licensing fees, hardware or cloud costs, and ongoing maintenance expenses. Calculate the potential return on investment (ROI) by weighing the benefits of enhanced security against the costs.
Challenges and Limitations of Web Application Firewalls
While Web Application Firewalls offer robust protection against a wide range of cyber threats, they are not without their challenges and limitations.
False Positives:
WAFs may occasionally block legitimate traffic, resulting in false positives. Striking the right balance between security and usability can be challenging.
Zero-Day Attacks:
WAFs primarily rely on known attack signatures, making them vulnerable to zero-day attacks—newly discovered vulnerabilities for which there are no predefined signatures.
Resource Intensive:
Implementing and managing a WAF can be resource-intensive. Organizations must allocate staff and resources for proper configuration, monitoring, and maintenance.
Overcoming Challenges:
To overcome these challenges, organizations can adopt a multi-layered security approach that combines WAFs with other security measures such as Intrusion Detection Systems (IDS), regular security audits, and employee training.
Emerging Trends and Future of Web Application Firewalls
As the threat landscape continues to evolve, Web Application Firewalls are adapting to meet new challenges. Here are some emerging trends in WAF technology:
Machine Learning and AI Integration:
WAFs are increasingly incorporating machine learning and artificial intelligence to enhance threat detection and reduce false positives. These technologies enable WAFs to adapt to evolving threats and learn from patterns of normal and malicious behavior.
Cloud-Native WAFs:
With the growing adoption of cloud computing, cloud-native WAF solutions are gaining popularity. These solutions are designed to seamlessly integrate with cloud environments and provide scalable, cloud-specific security.
API Protection:
As more applications rely on APIs (Application Programming Interfaces), WAFs are extending their protection to include API security. This is critical to safeguarding the connections between applications and services.
DevSecOps Integration:
DevSecOps practices are becoming more prevalent, integrating security into the development process. WAFs are evolving to fit within this framework, enabling organizations to build security into their applications from the outset.
Best Practices for Implementing and Managing WAFs
Implementing and managing a Web Application Firewall effectively requires following best practices to maximize the protection it offers. Here are some key guidelines:
Conduct a Risk Assessment:
Before implementing a WAF, assess your organization's specific risks and security requirements. Identify the critical assets and web applications that need protection.
Regularly Update WAF Rules:
Stay up-to-date with the latest threat intelligence and security updates. Regularly update your WAF's rules and policies to address emerging threats.
Monitor and Analyze Logs:
Continuously monitor WAF logs for unusual patterns or suspicious activities. Promptly investigate and respond to any alerts generated by the WAF.
Train Your Security Team:
Ensure that your security team is well-trained in WAF configuration and management. Investing in staff education can help you get the most out of your WAF solution.
Regularly Test and Evaluate:
Conduct regular penetration tests and vulnerability assessments to evaluate the effectiveness of your WAF. Identify and address any gaps in security.
Media Contact:
Company Name: Claight Corporation
Contact Person: Louis Wane, Corporate Sales Specialist – U.S.A.
Email: sales@expertmarketresearch.com
Toll Free Number: +1-415-325-5166 | +44-702-402-5790
Address: 30 North Gould Street, Sheridan, WY 82801, USA
Website: https://www.expertmarketresearch.com